What Supply Chain Attacks Teach Incident Responders: Key Points
- Supply chain attacks hide behind legitimate access, making early detection difficult and delaying response.
- Weak, distributed signals—not clear alerts—define the first hours of a supply chain incident.
- Scoping impact is complex because malicious activity often looks like normal behavior, requiring timeline-driven investigation.
- Containment is incremental and constrained by business dependency, forcing responders to balance risk reduction with operational continuity.
- Recovery is about rebuilding trust as much as restoring systems and often takes longer than traditional incident recovery.

Introduction
They exploit the same trust assumptions that organizations rely upon to operate efficiently. Yes, supply chain compromises are among the hardest attack patterns to identify during an incident.
From a cloud incident response perspective, the moment a trusted vendor becomes suspect often comes with the realization that the compromise has likely existed longer than anyone would like. In modern cloud and SaaS environments, supply chain attacks frequently originate through legitimate third-party integrations, federated identities, or approved software updates. Signed updates, approved tools, and long-standing third-party relationships are designed to enable scale and speed. Those same qualities, when abused, create ideal conditions for attackers to remain hidden.
The Mystery Thickens with Early Signals and False Positives
Unlike traditional intrusions, such as credential abuse or commodity malware, supply chain incidents rarely present as clear, high-confidence alerts. Instead, teams encounter subtle inconsistencies:
- A signed process initiating outbound connections outside its normal pattern
- A service account authenticating at unusual times
- A vendor-managed integration accessing systems beyond its expected scope
Because the activity originates from software that is explicitly trusted, suspicion is often delayed, a natural consequence of systems behaving exactly as they were designed to.
What makes these incidents particularly challenging is the uncertainty they introduce almost immediately. Responders must determine whether activity originated internally or was inherited, understand how far it may have propagated, and identify containment options that reduce risk without introducing unnecessary disruption. These decisions are often made with incomplete visibility, compounded by the opaque nature of third-party software. Recent attacks have reinforced a reality that incident responders have long understood: supply chain attacks are not exceptional. Trust itself must be treated as part of the threat model.
With most supply chain incidents, they do not begin with a definitive indicator so much as something that doesn’t fully align. Something is just off. It could be that a vendor service authenticates in a way that deviates slightly from baseline behavior, or a signed binary begins communicating with destinations it historically hasn’t.
Early in an investigation, it’s easy to attribute these signals to benign change, like:
- Configuration updates
- New features
- Undocumented dependencies
Endpoint controls validate signatures. Identity systems show legitimate credentials. And network telemetry reflects approved paths. What remains are low-confidence signals distributed across multiple data sources, with no single event clearly indicating compromise.
At this stage, responders are working through a narrowing investigative funnel.

Flags and Red Herrings
The first hours of response are defined by balance. Acting too conservatively allows malicious activity to blend into normal operations, but acting too aggressively risks disrupting essential services based on incomplete information. Experience from recent incidents consistently shows that waiting for certainty often means acting too late. In supply chain response, ambiguity itself is an investigative signal.
Once a supply chain compromise becomes a working hypothesis, the focus shifts to scoping — often the most complex phase of the response. Incident response teams must identify which systems consumed the affected software, when exposure began, and what level of access was inherited, all while assuming the initial deployment was legitimate and widespread. Asset inventories, deployment records, and change histories become as important as traditional security telemetry. Rather than looking for overt lateral movement, responders must determine how valid access may have been misused over time.
Because compromised services often operate entirely within expected permission boundaries, malicious activity can appear indistinguishable from normal behavior, such as:
- Authentication events succeed
- APIs respond as designed
- Downstream systems accept connections without challenge
Establishing impact requires correlating endpoint, identity, and network timelines to reconstruct how access was actually used. This process is rarely linear. Scope informs containment, containment reveals new scope, and timelines must be continuously refined as new information emerges.
In practice, the true blast radius is seldom clear at the outset.
Cordoning the Crime Scene: Attack Containment for Supply Chain Attacks
Containment decisions reflect this same complexity. Disabling a vendor dependency or rotating associated credentials may reduce exposure but can also introduce immediate operational impact. As a result, containment is often incremental rather than absolute. Access is constrained, credentials are rotated, network paths are segmented, and detections are refined to surface follow-on activity. These steps buy investigative time while preserving continuity where possible.
That containment path typically follows a staged progression:
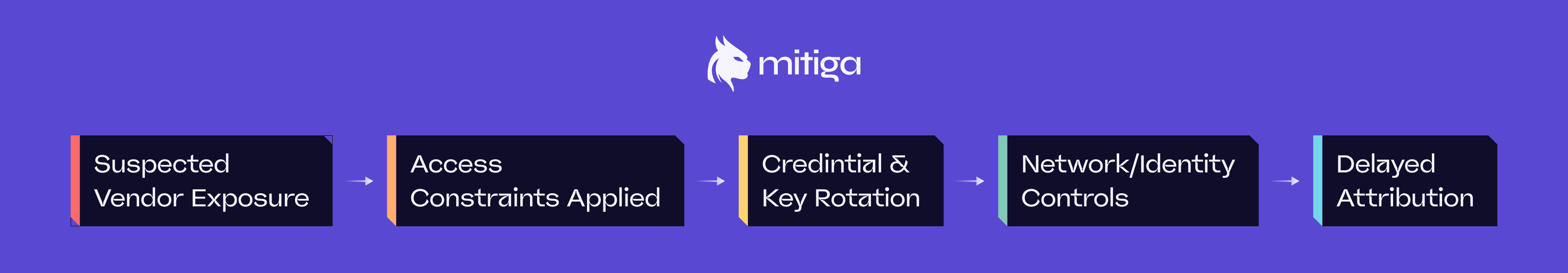
Visibility remains a limiting factor throughout the supply chain incident response. Many organizations lack deep insight into how third-party software behaves once deployed. Endpoint telemetry can confirm execution but not intent. Network logs may show destinations without revealing content. Identity logs record successful authentication without context around misuse. While vendor engagement can provide valuable insight, it often introduces latency and evolving narratives during active response. This reinforces the importance of internal telemetry and investigative rigor that treats third-party access with the same scrutiny as any external exposure.
The Recovery Period: Re-Establishing Confidence
Recovery from a supply chain incident extends beyond remediation. Teams must re-establish confidence in software integrity, credential hygiene, and update mechanisms that were previously assumed to be safe. This typically involves:
- Validating binaries,
- Redeploying trusted versions
- Rotating credentials at scale
- Reassessing access models
Even after operations normalize, uncertainty persists. Ensuring that compromised dependencies do not re-enter the environment through automated updates or inherited configurations often defines the length of recovery more than system availability itself.
Across recent cloud and SaaS security incidents, consistent patterns have emerged: delayed detection driven by implicit trust, difficulty scoping legitimate access paths, and containment constrained by business dependency. In response, organizations are increasingly focusing on preparedness — maintaining accurate vendor access inventories, tracking software provenance, improving identity and endpoint telemetry, and exercising supply chain scenarios as part of incident response planning. The most resilient teams are not those that assume compromise can always be prevented, but those prepared to investigate and respond decisively when trust fails.
What Supply Chain Attacks Mean for Incident Response Leaders
Supply chain incidents ultimately test an organization’s response maturity. They challenge visibility, coordination, and decision-making under uncertainty. From an incident response standpoint, success is defined by clarity of timeline, speed of investigation, and the ability to act without perfect information. Recent attacks have made one reality clear: trust is now part of the attack surface. Organizations that approach supply chain risk as an incident response problem — grounded in investigation, context, and operational reality — are better positioned to respond when, not if, that trust is abused.
LAST UPDATED:
February 19, 2026
Stop silent SaaS attacks before they matter.
If you don’t have visibility into your SaaS, cloud, AI, and identity all together, you won’t see the attack until it’s too late.
Take a look at some of Mitiga's latest resources.


