On September 6, Zoho released updates addressing a critical vulnerability in their password manager. According to the Cybersecurity and Infrastructure Security Agency (CISA), CVE-2021-40539 had already been actively exploited in the wild as a zero-day vulnerability. CISA advised admins to apply the patch immediately, as well as ensure that the AdSelfService Plus platform is not directly accessible from the internet. However, unpatched instances of the Zoho password manager continue to pose a threat as cyber attackers exploit the flaw in ManageEngine. On September 21, another article noted that advanced persistent threat (APT) actors are targeting academic institutions, defense contractors, and critical infrastructure in multiple industries. On Saturday, September 25, the Port of Houston was attacked using the Zoho vulnerability, but was able to fight the attack effectively. In November, researchers noted a new campaign exploiting the Zoho vulnerability by deploying the Godzilla webshell and exfiltrating data.
So, what risk does this vulnerability present, and can vulnerabilities in on-prem resources impact cloud environments as well?
Think about APIs
Zoho ManageEngine ADSelfService Plus is a self-service password management and single sign-on (SSO) solution for AD and cloud apps. CVE-2021-40539 is a REST API authentication bypass vulnerability in ManageEngine’s AdSelfService Plus platform that could allow remote attackers to bypass authentication and execute code remotely, giving attackers access across users’ Active Directory (AD) and cloud accounts.
The Zoho password manager REST API is useful for automating and integrating the password manager with other systems and services in a company’s environment. For instance, there may be a connection between the ticketing system and the password manager, so the help desk can issue password resets without giving those users direct access to the password manager. The problem is that the Zoho ManageEngine ADSelfService Plus REST API is not always turned off or restricted when not in use, especially when the Portal is internet-facing for employees to self-service password changes. This means that an unused feature could become a vulnerability if companies are not disabling, blocking, or restricting access to the REST API endpoint of Zoho’s password manager. To exploit this vulnerability, the attack creates a malicious URL that bypasses the system’s security filter due to an error normalizing URLs before validation. This leads to arbitrary file write permissions, which could be weaponized for commandline injection or the installation of webshells.
On-prem tools link to cloud credentials, too
Although the system in this case is itself an on-prem hosted resource, it can link to cloud credentials as well. For any organization that is using Zoho, chances are that they’ve taken their cloud access and put them into the password manager as well. Not only that, but attackers can also then move laterally from one cloud environment to another.
Linking and bundling access to segregated environments into a single platform is increasingly common as a way of managing and securing access credentials, and there are many advantages to doing so. It can improve user functionality and security, however, those benefits come with new risks as well. If that resource gets hacked, attackers can not only get to your on-prem resources, but can also pivot to SaaS and cloud providers, or other services linked to a user’s identity. It creates a single point of failure. If it is not clear yet, the first thing to do if you are impacted by this situation is to patch the vulnerability ASAP.
Cloud security does not eliminate the need for good cyber hygiene
Cloud vendors provide security in cloud environments, and they do an excellent job at handling many aspects of security, but it is not all the responsibility of the CSP; organizations using those CSPs have security responsibilities as well. Cloud security responsibility typically falls into different areas based on the cloud service model, but organizations are always responsible for people and data. The image below shows the responsibilities for AWS and their customers.
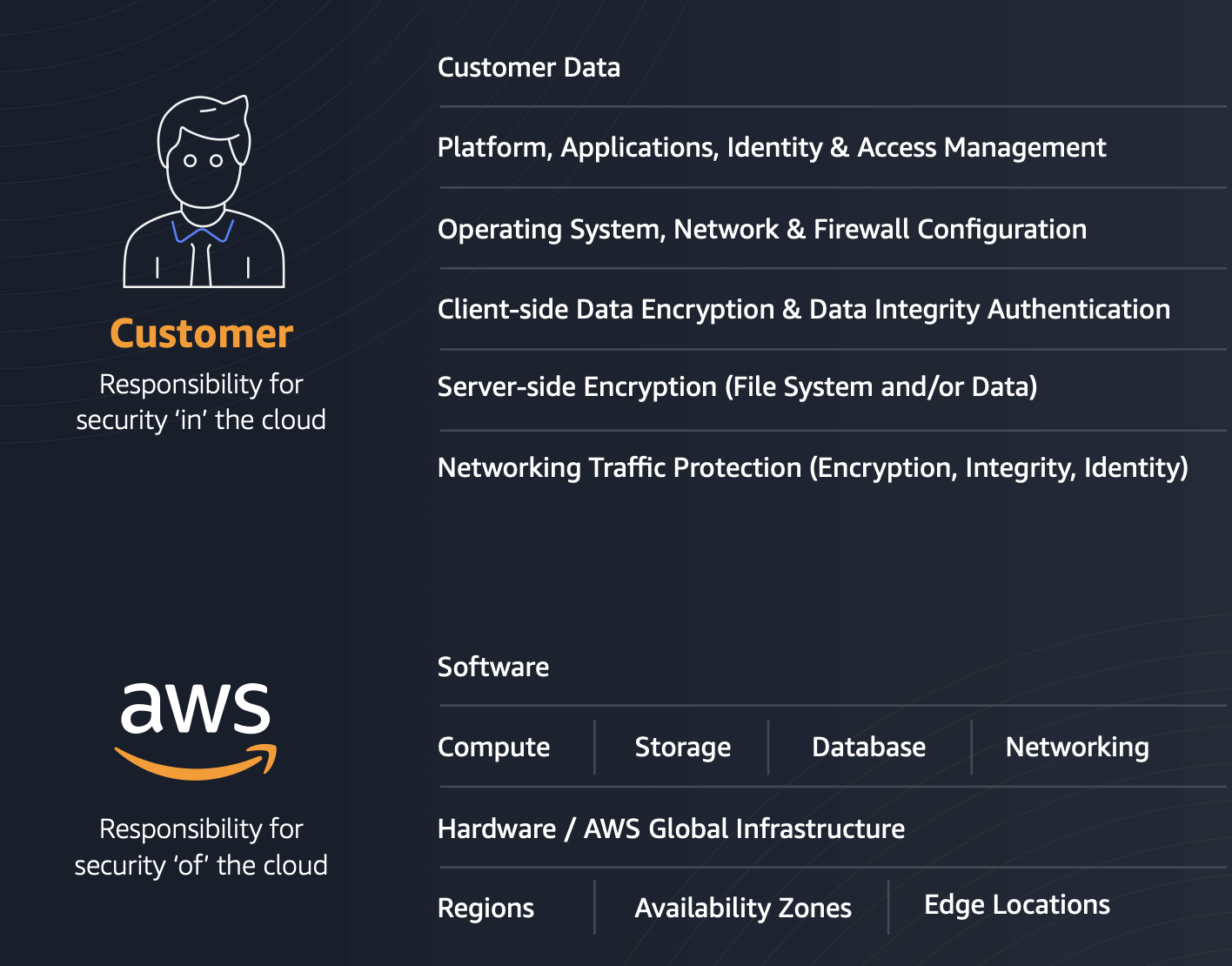
The Zoho vulnerability crosses from the security aspects your organization is responsible for into impacting security in the cloud. Despite all the protections from your CSP, this vulnerability means your cloud infrastructure is now vulnerable to compromise through credential theft. Cloud providers and SaaS providers handle patching the network, but it’s impossible for these providers to take responsibility for making sure that accounts don't get compromised or used by malicious actors. That responsibility lands on CSP customers.
Did you lock the door but leave the keys out?
Having all your account access managed by a password manager is a great way of managing and securing access in your environment. However, by putting all your eggs in one basket, you are potentially creating a single point of failure, and you should take extra precautions to secure it. If an attacker can gain access to the password manager the customer is using, they will be able to access resources as easily as a legitimate user. It is like locking all your doors, but then putting the keys in a little plastic bin on the driveway, right next to your carefully locked car and house.
Many of the security benefits of moving to cloud fall away if you are not securing your own access. Why pay for all that managed service if you are freely handing out access on your end? Remember, vulnerabilities in on-prem resources that enable access to your cloud devices help hackers unlock your virtual doors and not only infiltrate your on-prem environment, but your cloud environment as well.
3 things to add to your risk profiling priority list
If you are focused on improving risk profiling at your organization, here are a few things to add to your priority list:
- Have good basic security practices. Don’t leave a password manager open to the internet without understanding the risk, and properly restrict access or disable REST API services in your environment. Make sure you know whether there is a REST API attached to your password manager and how accessible it is. REST APIs are helpful in many ways, but they can also unintentionally increase your attack surface.
- Understand your products. In the case of the Zoho password manager, the ease of use for resetting a password from the website is helpful to end users, but being unaware of the potential implications of making it available on the internet is a significant problem. Even with a known vulnerability, if an organization did not open access up to the password manager over the internet and did not have the REST API accessible, the likelihood of being impacted by a similar zero day go down significantly.
- Incident Readiness is essential. You cannot protect from a zero day because you don't know about it, so you need to prepare for attacks. Make sure you take the time to create an Incident Response plan that includes provisions for resetting the impacted environments and recovering from an incident.
New vulnerabilities are disclosed regularly, and some of them are zero- and one-day events, when there’s very little time to apply patches or implement new security measures. Incident readiness helps you accelerate recovery and increase your resiliency to future attacks.

LAST UPDATED:
March 3, 2025


