In this cloud-first world we live in, security teams face an impossible equation: protect the rapidly growing Cloud and SaaS footprint with the same limited resources. At Mitiga, we've recognized this fundamental challenge from day one, which is why we're excited to announce the next evolution of our AI technology: Helios AI.
The Cloud Security Challenge: Scale vs. Speed
The modern cloud attack surface generates hundreds of activities per day across multi-cloud and SaaS environments. For security teams, this creates a critical dilemma:
- Too much noise: Seemingly legitimate activities still need to be vetted, and they outnumber actual threats by orders of magnitude
- Too much complexity: Advanced threats, targeted attacks, and insider threats materialize faster and can blend seamlessly with normal operations
- Too little time: Manual triage consumes valuable analyst hours, inherently prioritizing focus on high-severity threat leads and creating opportunities for sophisticated attacks to hide undetected

Introducing Helios AI: Your Cloud SecOps Co-Pilot
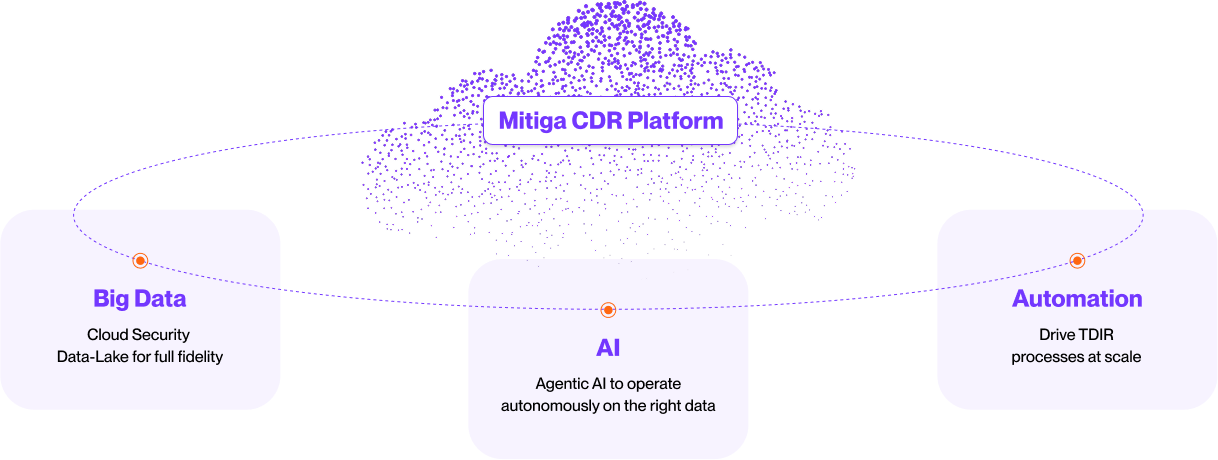
Helios AI is the culmination of our AI-first approach to cloud security. While many vendors are hastily adding AI capabilities, Mitiga built our platform – from its inception – on three fundamental technologies:
- Cloud-native data lake architecture delivering full-fidelity context at an economical cost—while enhancing AI accuracy
- Advanced AI engines that perform real-time analyses on all data in our comprehensive cloud data lake to identify even the most elusive suspicious or malicious activities
- End-to-end automation that enables work at scale to cover more ground and eliminate repetitive manual tasks
Helios AI leverages these foundations to deliver a true force multiplier for your Cloud and SaaS Threat Detection, Investigation, and Response (TDIR) operations.
AI Insights: Our First Helios AI SecOps Assistant Functionality
Today, we're releasing the first Helios AI capability: AI Insights. This breakthrough feature:
- Dynamically adjusts risks while automatically executing dozens of contextual triage tests against every potential threat lead or significant activity in the cloud
- Intelligently separates routine activities from risky operations done unintentionally by your team to genuine security concerns
- Provides analysts with pre-assembled extensive evidence packages for rapid decision-making that would otherwise take hours to produce
- Dynamically adjusts risks while automatically executing dozens of contextual triage tests against every potential threat lead or significant activity in the cloud
- Intelligently separates routine activities from risky operations done unintentionally by your team to genuine security concerns
- Provides analysts with pre-assembled extensive evidence packages for rapid decision-making that would otherwise take hours to produce
How Helios AI Works: Intelligence Across the Detection Lifecycle
What makes Helios AI different is its integration across the entire threat detection lifecycle:
Research Intelligence
Our threat research team uses Helios AI to analyze billions of cloud events across our comprehensive data lake, identifying subtle attack patterns that human analysts might miss. Helios helps formulate precise Indicators of Attack (IoAs) based on real-world cloud attack techniques.
Detection Rollout and Refinement
Before deployment, Helios AI validates each detection rule, automatically tuning parameters to maximize detection efficacy while minimizing noise.
Runtime Analysis
In production, Helios AI doesn't just trigger alerts - it performs real-time triage, assembling context, validating assumptions, and adjusting confidence scores. When suspicious activity is confirmed, SecOps teams receive automatically crafted attacker timelines (rather than raw alerts) that span multiple environments.
The Future of Cloud Security Operations
Helios AI represents our vision for cloud detection and response: intelligent systems working alongside human experts, each doing what they do best. The machines handle scale, repetition, pattern recognition, and anomaly detection, while your team focuses on critical decisions and strategic tasks.
In the coming months, we'll be expanding Helios AI capabilities to increase its autonomous work and intelligent auto-responses.
Experience the Difference
Cloud security doesn't have to mean choosing between comprehensive coverage and operational efficiency. Mitiga's Helios AI is here to help you achieve both.
LAST UPDATED:
January 15, 2026


