Key Points
- A phishing email granted attackers access to a rogue OAuth app, leading to persistent control of a victim’s mailbox through Microsoft Graph API.
- Attackers extracted AWS access keys from emails, then used Scout Suite to perform reconnaissance in the sandbox environment.
- A misconfigured trust relationship allowed privilege escalation from sandbox to production, resulting in full AWS infrastructure takeover.
- Forensic evidence showed attacker activity across OAuth permission grants, Graph API queries, email access, and AWS role assumptions.
- Strategic defenses include stronger OAuth governance, phishing awareness training, credential vaulting, and enhanced monitoring of Graph API and AWS logs.
The Phishing Wake-Up Call: Rogue OAuth App Breach in Action
In a recent incident response investigation, Mitiga uncovered a chilling attack that started with a single compromised email inbox and spiraled into a full-blown takeover of an organization's cloud infrastructure.
The culprits? A rogue OAuth application and a series of clever moves by attackers who turned a phishing email into a master key for the victim’s AWS environment.
This blog post breaks down how the attack unfolded and provides practical recommendations to protect your organization from similar threats.
Phishing Incident Overview: How the Rogue OAuth App Attack Began
The incident began with a targeted email phishing campaign that tricked a user into granting permissions to a rogue OAuth application registered in Microsoft Azure. This initial compromise provided the attackers with persistent access to the victim’s email account, allowing them to search for and extract sensitive information, including AWS access keys for a sandbox environment.
Armed with the access keys, the attackers conducted reconnaissance and discovered a trust relationship between the sandbox and production environments. This allowed them to escalate privileges and gain complete control over the organization's AWS infrastructure.
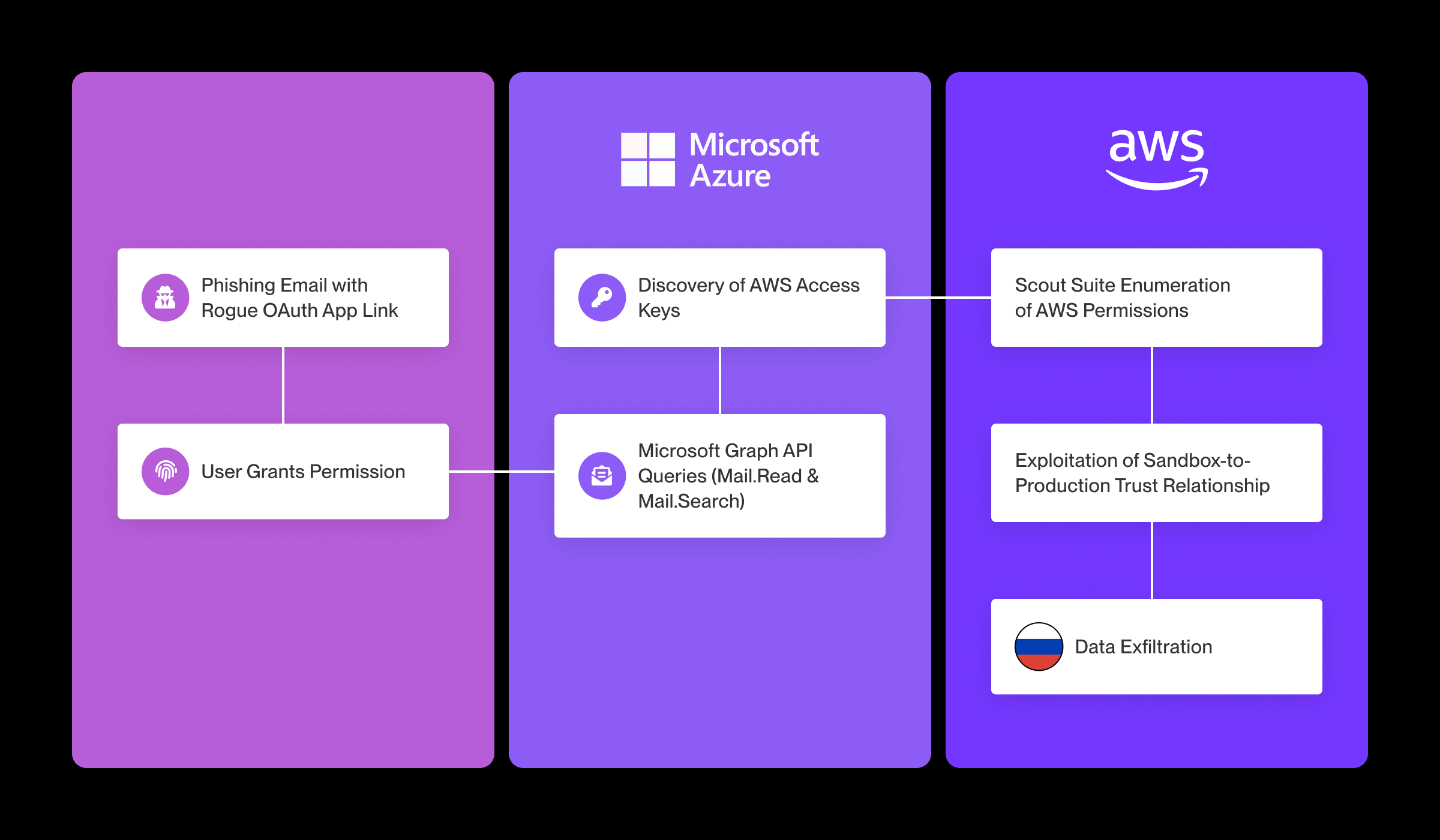
Step-by-Step Phishing Attack Progression
- Initial Compromise: The victim clicked a phishing link from a suspicious email delivered by the attackers, granting permissions to the rogue OAuth. The app used the Microsoft Graph API for persistent mailbox access, allowing the attackers to read emails and perform searches without further user interaction.
- Mailbox Exploitation: The attackers used POST requests via the Graph API to search the mailbox for sensitive information. While the specific keywords searched were not visible in the logs due to the POST method, the logs recorded the emails accessed by the attackers.
- Credential Discovery: The attackers discovered AWS access keys for a sandbox environment within the compromised mailbox.
- AWS Reconnaissance: Using the stolen AWS keys, the attackers employed Scout Suite, an open-source cloud security auditing tool, to enumerate permissions within the AWS sandbox environment.
- Privilege Escalation: The attackers discovered a trust relationship between the sandbox and production environments, exploiting this misconfiguration to escalate privileges and gain unauthorized access to the production AWS infrastructure.
- Data Exfiltration: The attackers exfiltrated sensitive data from the production environment, with network traffic originating from Rostelecom IP addresses.
Forensic Evidence from the Security Breach
Investigation relied heavily on available forensic data to piece together the attacker’s actions. To provide insight into the investigation process, let’s look at some sanitized excerpts of key log records that highlight critical stages of the attack.
1. Permission Granting to Malicious OAuth Application
This entry shows the victim granting permissions to the rogue OAuth app, establishing the initial compromise.
{
"EventTime":"X",
"Scope":["Mail.Read","User.Read","offline_access",
"openid","profile"],
"event_name":"Add delegated permission grant.",
"TargetServicePrincipalName":"[Rogue OAuth App Name]",
"UserKey":"[Victim User Key]"
}
2. Graph API Query Execution
This log entry captures the attacker's use of the Graph API to search the mailbox, with the POST method hiding specific query details.
{
"EventTime":"X",
"requestMethod": "POST",
"requestUri":"https://graph.microsoft.com/beta/search/query",
"appId":"[Rogue OAuth App ID]",
"ipAddress":"185.100.X.X. (Rostelecom)",
"userAgent":"python-requests/2.31.0",
"apiVersion":"beta"
}
3. Graph API Email Access
Right after the repetitive queries, the attacker commenced the extraction of email content, highlighting their intent to target sensitive information.
{
"EventTime":"X",
"requestMethod": "GET",
"requestUri":"https://graph.microsoft.com/v1.0/me/messages/
[Message ID]",
"appId":"[Rogue OAuth App ID]",
"ipAddress":"185.100.X.X. (Rostelecom)",
"userAgent":"python-requests/2.31.0",
"apiVersion":"beta"
}
4. Scout Suite Usage in AWS
AWS CloudTrail shows the attackers using stolen credentials to run Scout Suite, enumerating permissions in the sandbox environment.
{
"eventTime":"X",
"src_ip":"185.100.X.X. (Rostelecom)",
"src_useragent":"Scout-Suite/5.13.0 md/Botocore#1.34.74 ua/
2.0 os/linux#4.4.0-26100-Microsoft md/arch#x86_64 lang/
python#3.10.12 md/pyimpl#CPython cfg/
retry-mode#legacy Scout Suite/5.13.0
(https://github.com/nccgroup/ScoutSuite)",
"accessKeyId":"[Stolen AccessKeyId]"
}
5. Exploitation of Trust Relationship
This entry shows the attacker leveraging the trust relationship to assume a role in the Production account.
{
"eventTime":"X",
"src_ip":"185.100.X.X. (Rostelecom)",
"eventName":"AssumeRole",
"EventSource":"sts.awsamazon.com",
"RequestParameters":{
"roleArn":"arn:aws:iam:
[Sanitized Production Account ID]:role/[Role Name]",
"roleSessionName":"[Session Name]"
}
Strategic Recommendations to Reduce Risk of Rogue OAuth App Attacks
OAuth App Governance
- Implement a strict approval process for third-party OAuth applications.
- Regularly audit and revoke unnecessary app permissions in Microsoft Azure.
Phishing Defense
- Enhance user training to recognize fraudulent email addresses and suspicious links.
- Deploy advanced email filtering within user email clients or at the server level to detect and block malicious OAuth application links.
Credential Management
- Prohibit storing sensitive credentials, such as AWS access keys, in email or unsecured locations.
- Use a secure vault solution for managing and rotating access keys.
Monitoring and Detection
- Enable detailed logging for Microsoft Graph API and AWS activities to capture suspicious behavior.
- Implement real-time alerts for unauthorized OAuth app activity and anomalous cloud access.
Conclusion: Why Rogue OAuth App Threats Require Attention
This incident shows how a single email can lead to a cloud infrastructure compromise if combined with weak app governance and misconfigured trust relationships, underscoring the risk posed by rogue OAuth applications and the importance of securing cloud environments against lateral movement.
By addressing the identified misconfigurations, such as permissive OAuth apps, exposed credentials, and misconfigured trust relationships, organizations can significantly reduce the risk of similar attacks. Robust monitoring and attribution is essential to detecting and responding to threats effectively.
LAST UPDATED:
November 18, 2025


