In a cybersecurity landscape that seems ever volatile, the Midnight Blizzard attack against Microsoft stands out for its simplicity, strategic execution, and the implications it holds for global cybersecurity. Orchestrated by APT29, also known as Cozy Bear, this campaign not only underscores the advanced capabilities of state-sponsored actors, but also serves as a critical learning opportunity for organizations worldwide.
The Prelude: Identifying the Adversary
APT29, a moniker synonymous with the Russian Foreign Intelligence Service (SVR), has been at the forefront of cyber espionage since its inception around 2008. Known for its stealth and patience, APT29 targets political, economic, and military intelligence to further Russia's global influence. This group's history of high-profile breaches includes the infamous 2016 DNC hack and the SolarWinds supply chain attack, displaying a penchant for long-term strategic access over quick gains.
The Breach Mechanics: A Step-by-Step Breakdown
Initial Access via Password Spraying
Tactic: Initial Access (TA0001)
Technique: Password Spraying (T1110.003)
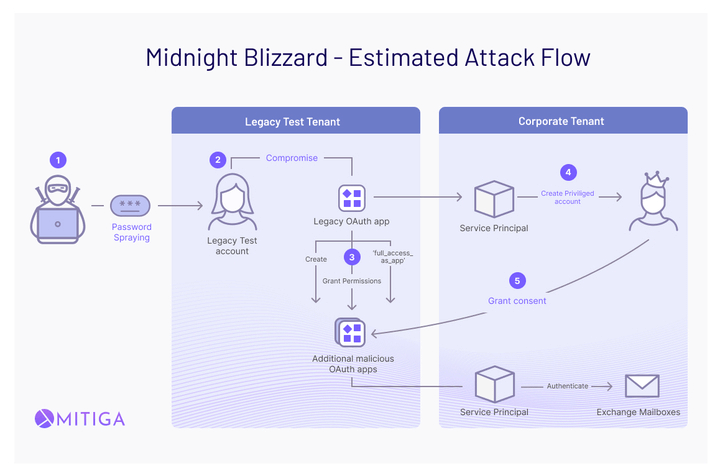
Expanding on the initial step of the Microsoft breach, this provides a deeper look into the attackers' methodologies and the vulnerabilities they exploited. The term "password guessing" mentioned in the document refers to the systematic approach used by the attackers to identify weak, commonly used passwords across multiple accounts. This method is particularly effective against accounts lacking robust security measures like Multi-Factor Authentication (MFA), which was the case with the targeted "test" tenant within Microsoft's environment.
This first step is crucial for understanding the attackers' entry point. By selecting a non-production test tenant, they exploited a less fortified segment of Microsoft's digital estate, where security protocols might not be as stringent as in production environments. The choice of a test tenant likely stemmed from the assumption that these environments are often overlooked in security operations, making them more vulnerable to such attacks.
The success of this initial access did not just hinge on the ability to guess passwords but also on the strategic selection of the target. Test tenants, by their nature, are used for development, testing, and other non-production purposes, which can sometimes lead to lax security practices, such as the absence of MFA. This oversight provided a foothold for the attackers, allowing them to leverage this access for further exploitation within Microsoft's corporate network.
Compromising an App Registration
Tactic: Privilege Escalation (TA0004)
Technique: Account Manipulation: Additional Cloud Credentials (T1098.001)
Compromising an app registration involves a strategic manipulation of existing configurations by the attackers to secure elevated access within the Microsoft corporate environment, specifically within the test EntraID tenant. This step illustrates a sophisticated understanding of the target's internal systems and the utilization of legacy components to breach security perimeters.
Acquiring Access Tokens:
The attackers began by acquiring an access token using the credentials of the compromised OAuth test application. This token provided access to the corporate tenant, leveraging previously granted elevated permissions. The command executed (curl -X POST...) signifies a direct and methodical approach to authenticate against Microsoft's OAuth endpoint, highlighting the attackers' technical sophistication and their understanding of cloud authentication
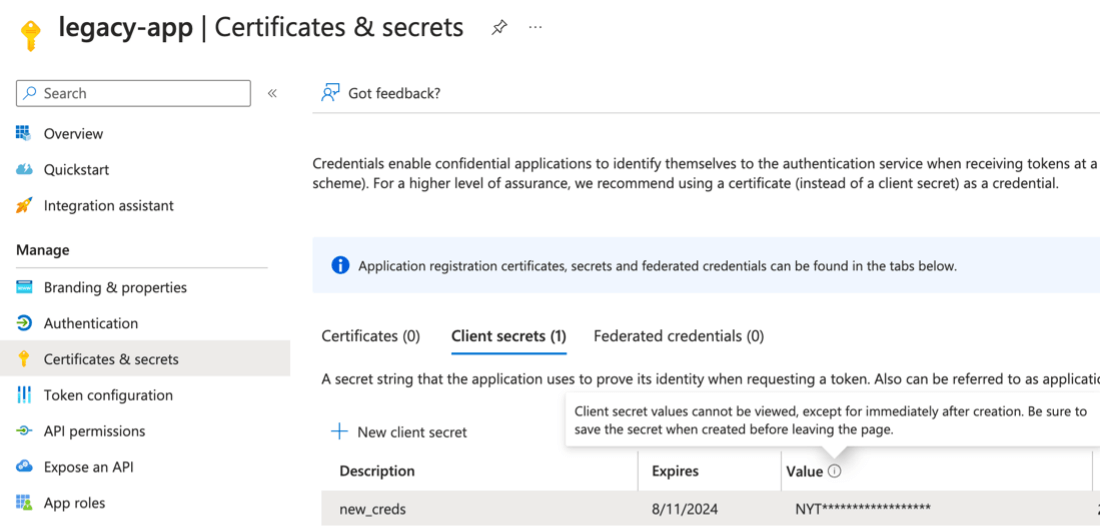
This suggests that this "Legacy App" service principal was likely assigned one of several high-privilege EntraID roles, such as Global Administrator, Partner Tier2 Support, or Privileged Role Administrator. Alternatively, it might have been granted powerful MS Graph app roles, specifically "AppRoleAssignment.ReadWrite.All" or "RoleManagement.ReadWrite.Directory" These roles and permissions are indicative of a broad scope of access within the corporate tenant, potentially up to Global Administrator rights or an equivalent level of control.
This maneuver highlights a critical risk in how legacy systems and applications can be exploited to bypass modern security measures. The "AppRoleAssignment.ReadWrite.All" role, in particular, suggests the attackers could assign app roles and manage permissions across the tenant, a capability that would significantly amplify their access and control over corporate resources.
Elevation and Expansion
Tactic: Privilege Escalation (TA0004)
Technique: Account Manipulation: Additional Cloud Roles (T1098.003)
The adversaries utilized their foothold within the Microsoft environment to significantly escalate their access and expand their control. This phase of the attack intricately demonstrates the attackers' adeptness in navigating and exploiting the cloud infrastructure, specifically through the manipulation of Microsoft Graph (MS Graph) permissions.
The Process of Elevation and Expansion:
The attackers took advantage of a "legacy" app, originally part of the test tenant, and leveraged it to gain a foothold within the corporate tenant. This action involved instantiating the legacy app as a service principal in the corporate environment, which implies a deep knowledge of Microsoft's identity and access management systems. By doing so, they effectively bridged the gap between a less secure testing environment and the highly sensitive corporate ecosystem.
Creating a New User:
With the acquired access token, the attackers executed a critical move by using the Directory.ReadWrite.All permission. This permission enabled them to create a new user within the corporate tenant. The creation of a new user account under their control marked a significant escalation in the attack, providing a fresh and fully controlled entry point into the corporate environment.
Assigning Global Administrator Role (or another high permissive role):
The culmination of their elevation strategy involved utilizing the RoleManagement.ReadWrite.Directory permission to assign the newly created user the Global Administrator role. This action effectively granted the attackers a high level of control over the corporate environment, allowing them unrestricted access to resources within the tenant.
Strategic Use of OAuth Applications:
The report hints at the creation of additional OAuth applications, which, while not explicitly linked to the compromised test app or user, suggests a broader strategy to embed multiple backdoors within the environment. These actions likely served to complicate detection and eradication efforts, ensuring persistent access for the attackers.
Implications:
This phase of the attack underscores the critical importance of securing and monitoring MS Graph permissions, the management of OAuth applications, and the assignment of roles within cloud environments. It highlights the necessity for organizations to rigorously apply the principle of least privilege, conduct regular audits of permissions and roles, and implement robust monitoring to detect anomalous activities indicative of such sophisticated exploitation tactics.
Creation of Malicious App Registrations
Tactic: Defense Evasion (TA0005)
Technique: Create Account: Cloud Account (T1136.003)
The attackers further entrenched their presence within Microsoft's infrastructure through a calculated and methodical approach. This phase illustrates a deepening of their attack strategy, moving beyond initial access and privilege escalation to establish mechanisms for persistence, broader access, and potentially, further exploitation.
Detailed Actions Taken:
Series of Malicious OAuth Applications:
The attackers created a series of malicious OAuth applications. This move was not merely opportunistic but a calculated effort to diversify their access points within the target environment. By establishing multiple OAuth applications, they effectively created several backdoors, each capable of independently maintaining access to the compromised environment. This redundancy ensures that even if one application is discovered and neutralized, others remain active, complicating the defender’s task of fully eradicating the attackers' presence.
Creation of a New User Account:
To facilitate access for these malicious applications, the attackers created a new user account within the Microsoft corporate environment. This step was crucial as it provided a seemingly legitimate identity through which the malicious applications could be granted access permissions. The creation of a new user, particularly with administrative privileges, underscores the attackers’ ability to manipulate the environment’s identity and access management systems to their advantage.
Granting Extensive Permissions to Malicious Apps:
The newly created OAuth applications were granted the full_access_as_app role for Office 365 Exchange Online. This permission is particularly significant because it typically allows extensive access and privileges to an application, in this case, enabling the attackers to access target mailboxes. Granting such a high level of access to newly created unauthorized applications demonstrates the attackers' comprehensive understanding of the permissions model and their ability to exploit it for maximal access.
Strategic Implications:
The creation of malicious OAuth applications and the granting of extensive permissions to them are indicative of a sophisticated understanding of cloud-based identity and access management. It also reflects a strategic approach to maintaining persistence within the compromised environment. By leveraging the OAuth framework, the attackers ensured that their access was not only broad but also deeply embedded within the fabric of the corporate infrastructure, making detection and remediation more challenging.
This step highlights the necessity for organizations to rigorously monitor and audit the creation and permission granting of OAuth applications within their environments. It also underscores the importance of anomaly detection mechanisms that can identify unusual patterns of behavior, such as the creation of multiple applications in a short period or the assignment of high-level permissions to new or low-reputation applications.
New User Creation for Consent
Tactic: Collection (TA0009)
Technique: Abuse Elevation Control Mechanism (T1548)
The attackers leveraged the newly created user to navigate the OAuth architecture intricately, underscoring their methodical approach to deepen their access and establish persistence within the Microsoft corporate tenant.
Detailed Actions Taken:
Utilization of Newly Created User:
The newly created user, crafted with administrative privileges in earlier steps, was utilized to consent to the malicious app registrations. This step is a testament to the attackers' strategic foresight, as it exploited a fundamental aspect of the OAuth architecture—allowing users to consent to OAuth applications without requiring special privileges, provided the applications request permissions that do not necessitate admin consent.
Service Principal Creation:
The consent granted by the newly created user led to the establishment of a service principal for each malicious app registration within the Microsoft corporate tenant. This action effectively bridged the gap between the seemingly benign new user and the malicious applications, embedding the attackers' tools directly within the corporate infrastructure.
Credential and Authentication Strategy:
With the service principals in place, the attackers were then able to add credentials to their app registrations in the "test" tenant and use those credentials to authenticate as the apps’ associated service principals in the "prod" tenant. This demonstrates a sophisticated understanding of cloud authentication mechanisms and illustrates the attackers' ability to manipulate these mechanisms to their advantage.
Strategic Implications and Security Considerations:
The step underscores the critical need for strict controls and oversight on the consent and authentication processes within cloud environments. It highlights the potential for attackers to exploit the integrated nature of cloud services and the OAuth consent model to establish footholds and move laterally within targeted environments.
It also points to the importance of monitoring for unusual consent requests and the creation of new users with administrative privileges, especially when linked to app registrations. Organizations should consider implementing policies that require admin approval for certain high-risk permissions and closely monitor the service principals and their associated permissions within their environments.
This phase of the attack not only solidifies the attackers' presence within the target environment but also showcases their methodical planning and execution, leveraging the built-in features of cloud platforms to bypass traditional security controls. The ability to consent to OAuth applications, a mechanism designed for ease of use and integration, is here turned into a vector for establishing persistence and control.
Granting "Full Access as App" Role
Tactic: Exfiltration (TA0010)
Technique: Account Manipulation: Additional Cloud Roles (T1098.003)
The attackers finalized their strategic maneuver to gain extensive access to Microsoft's corporate mailboxes, exploiting the elevated privileges they had meticulously acquired in the preceding steps. This phase is a critical culmination of their efforts, demonstrating their sophisticated understanding of Microsoft's permission model and their ability to manipulate it for malicious purposes.
Detailed Actions Taken:
Utilization of Office 365 Exchange Online Permissions:
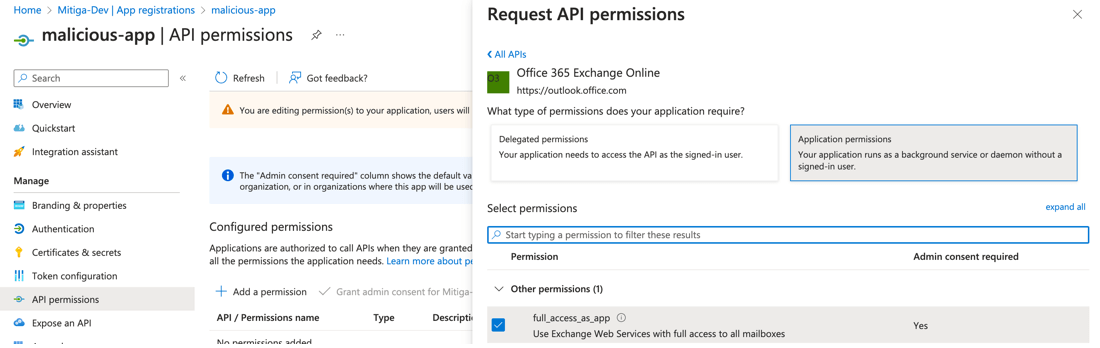
The adversaries exploited the "full_access_as_app" permission of Office 365 Exchange Online. This permission, which requires administrative consent, was presumably granted using the admin privileges of the newly created user in the corporate environment. This step underscores the high level of access the attackers had achieved, allowing them to tap directly into Microsoft's email system to access corporate mailboxes.
Strategic Abuse of MS Graph Permissions:
To facilitate this, the attackers had likely been granted, or had managed to assign themselves, critical MS Graph app permissions such as Directory.ReadWrite.All, RoleManagement.ReadWrite.Directory, and notably, AppRoleAssignment.ReadWrite.All. These permissions collectively enabled the creation of new users, assignment of directory roles, and manipulation of app permissions, laying the groundwork for this final step.
Execution and Access Token Acquisition:
With the permissions in place, the attackers proceeded to create a new multi-tenant OAuth application and assigned it the "full_access_as_app" permission. This malicious app, created under the guise of legitimacy through the abused permissions, was then used to request an access token. This token provided the attackers with the means to access any mailbox within the corporate tenant, effectively breaching the confidentiality of Microsoft's internal communications.
Strategic Implications and Security Considerations:
This step illustrates a profound exploitation of the integrated OAuth and permission model within Microsoft's cloud environment. It highlights the critical importance of closely monitoring and controlling the assignment of application permissions, especially those that confer extensive access to sensitive resources like email.
It underscores the necessity for a robust administrative consent process for app permissions, particularly for permissions that allow access to critical data and systems. Organizations should consider implementing stricter controls and oversight mechanisms, including the review of consent grants and the monitoring of newly created applications within their environments.
This phase of the attack, by granting the "full_access_as_app" role to malicious applications, marks the attackers' transition from gaining and expanding access to executing their objective of data exfiltration. It serves as a stark reminder of the importance of vigilance in managing permissions and the need for comprehensive security measures to safeguard against such sophisticated attacks.
A Call to Action
The Midnight Blizzard attack on Microsoft is a stark reminder of the ever-present threat posed by state-sponsored actors. It underscores the importance of vigilance, proactive defense strategies, and the need for a collective effort in cybersecurity. Organizations must not only focus on fortifying their defenses but also on sharing knowledge and strategies to mitigate such threats effectively.
What now?
Some key actionable recommendations:
What’s Mitiga’s answer to attack methodologies like the Microsoft breach?
In response to the sophisticated attack methodologies outlined above, Mitiga has taken proactive and comprehensive steps to ensure that organizations are equipped to detect, prevent, and respond to similar threats. Understanding the intricacies of these attacks, Mitiga has developed and deployed dedicated new indicators of attack (IOAs) specifically designed to identify each step of the discussed attack flow such as granting high-risk permissions to service principals, and anomalous detection of applications accessing mail items within the organization.
These IOAs are a testament to Mitiga's commitment to staying ahead of evolving cyber threats, providing an essential layer of detection that is finely tuned to the nuances of these sophisticated attacks.
Mitiga's product now boasts full coverage for all the related Tactics, Techniques, and Procedures (TTPs) associated with the attack. This extensive coverage ensures that organizations can rely on Mitiga's platform to not only detect but also understand and mitigate threats based on the most current and relevant attack vectors. By integrating detailed knowledge of these TTPs, Mitiga's solution empowers clients to swiftly identify potential breaches, assess their impact, and take decisive action to secure their environments.
Furthermore, recognizing the importance of timely and expert intervention, Mitiga's professional threat hunting team has taken a hands-on approach with all existing clients. Through "Event-driven hunts," the team is meticulously searching for signs of the outlined attack within client environments. This proactive search is not a mere precaution but a critical step in identifying potential vulnerabilities and threats before they can be exploited. Following these hunts, Mitiga has provided clients with detailed results, offering insights into their security posture and recommending specific actions to address any identified risks.
These initiatives by Mitiga underscore a holistic approach to cloud security, blending advanced technological solutions with expert human analysis. By dedicating resources to the development of new IOAs, ensuring comprehensive coverage of relevant TTPs, and actively engaging in threat hunting, Mitiga offers a robust defense mechanism against complex cyber threats. This commitment ensures that clients are not only protected against the specific steps of the discussed attack but are also equipped to face a broad spectrum of cybersecurity challenges.
LAST UPDATED:
June 23, 2025


